![]()
![]()
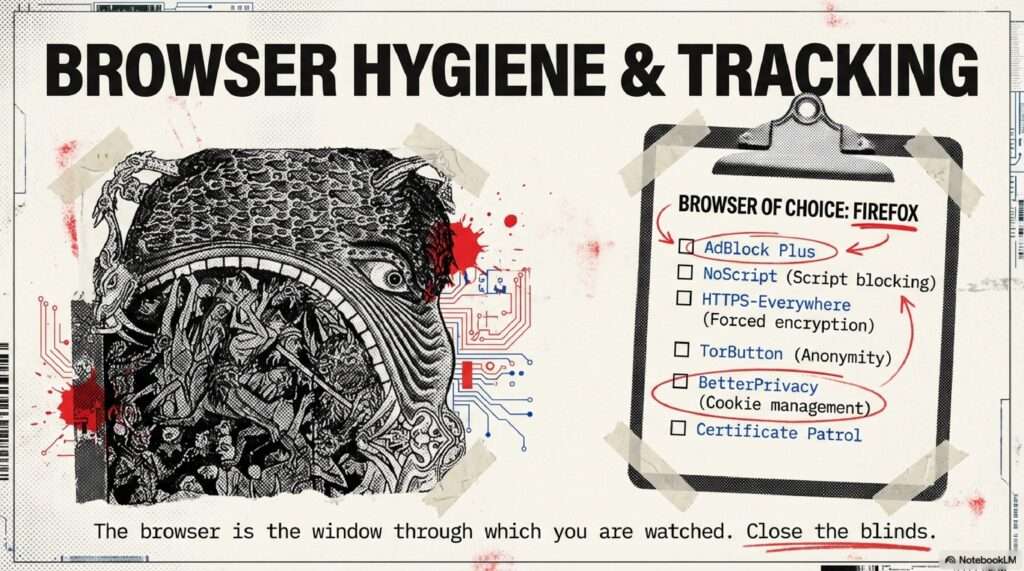
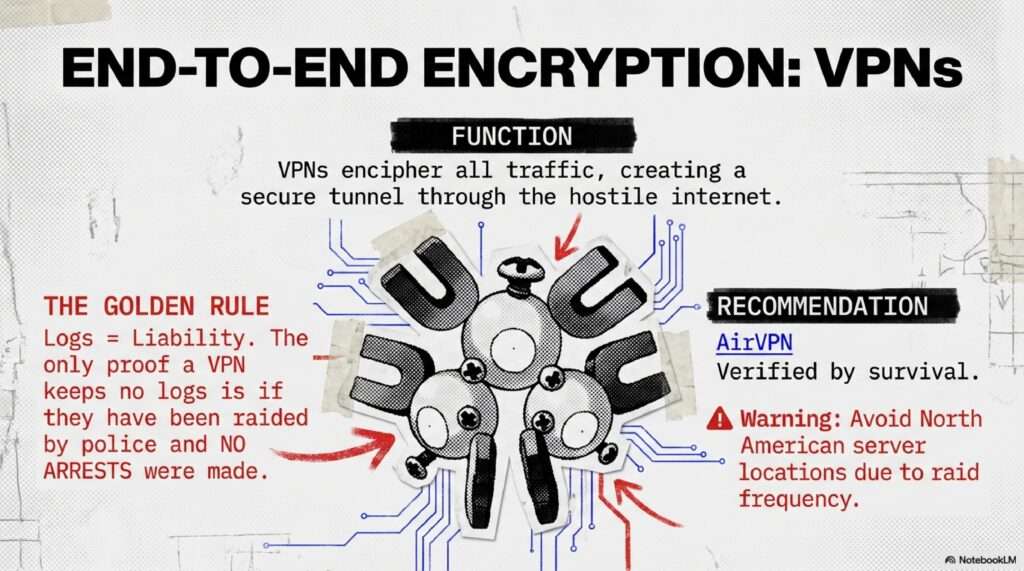

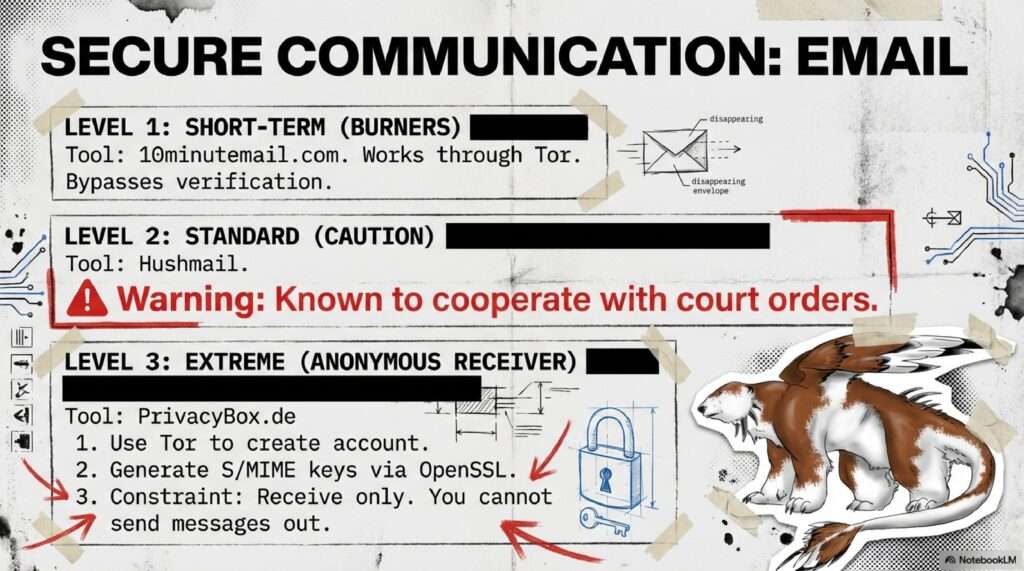

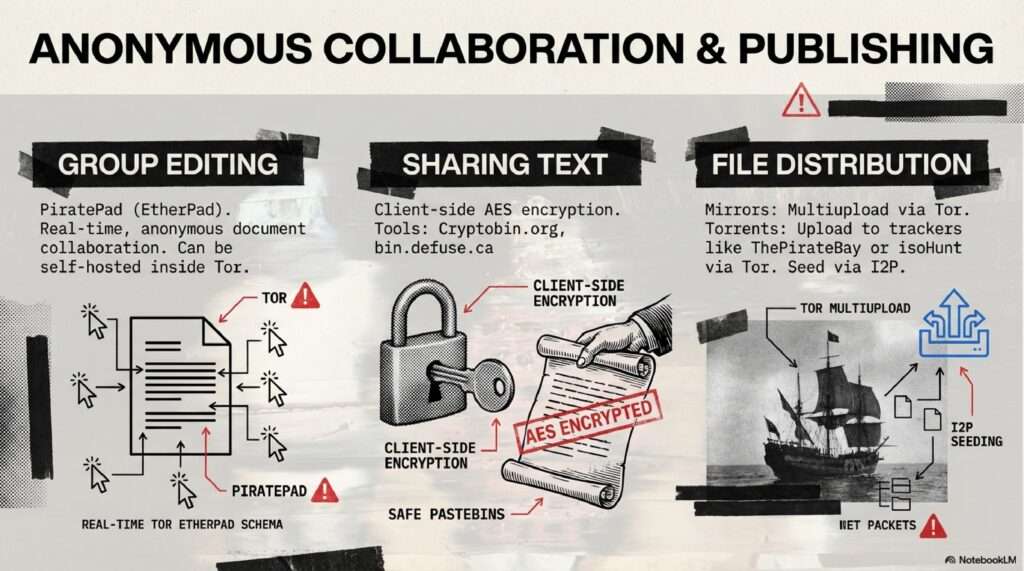


Cryptomorphosis: Navigating the Era of Total Observation
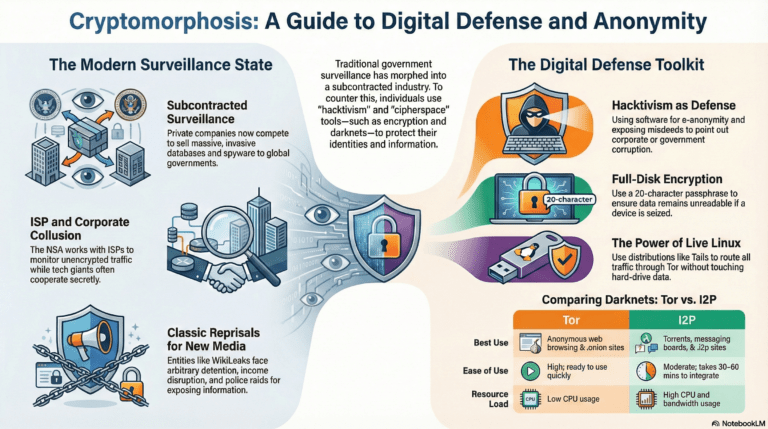
The digital frontier of 2026 is no longer a static landscape; it is a fluid environment of constant observation. Cryptomorphosis is the tactical evolution required to survive this shift. It is the art of transforming your digital presence from a vulnerable, trackable target into a dynamic, “shape-shifting” entity.
The Three Pillars of Digital Shape-Shifting
To achieve true operational security in cipherspace, you must master the three core components of identity fluididty:
-
Identity Decoupling: Severing the link between your physical person and your digital “Handle.”
-
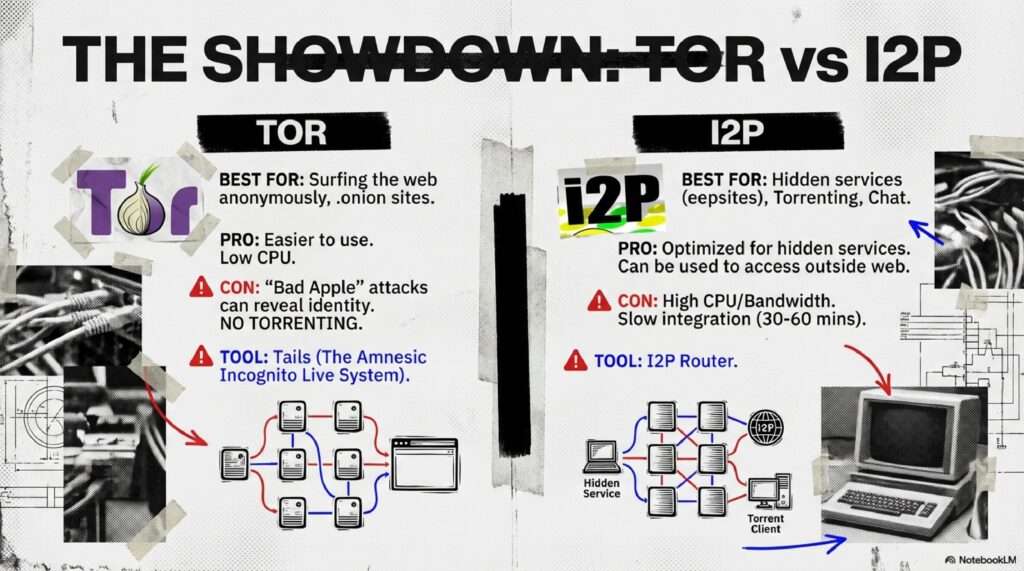
Architectural Resilience: Utilizing decentralized networks like I2P and Meshnets to bypass centralized “choke points.”
-
Encrypted Persistence: Implementing Post-Quantum Cryptography (PQC) and short-lived S/MIME certificates to protect against “store now, decrypt later” threats.
The 2026 Survival Strategy
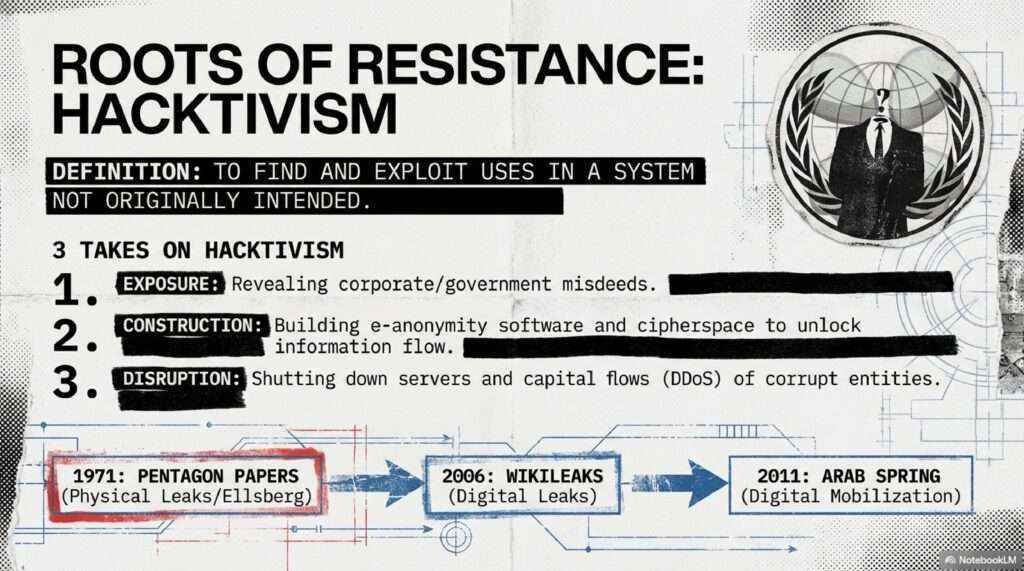
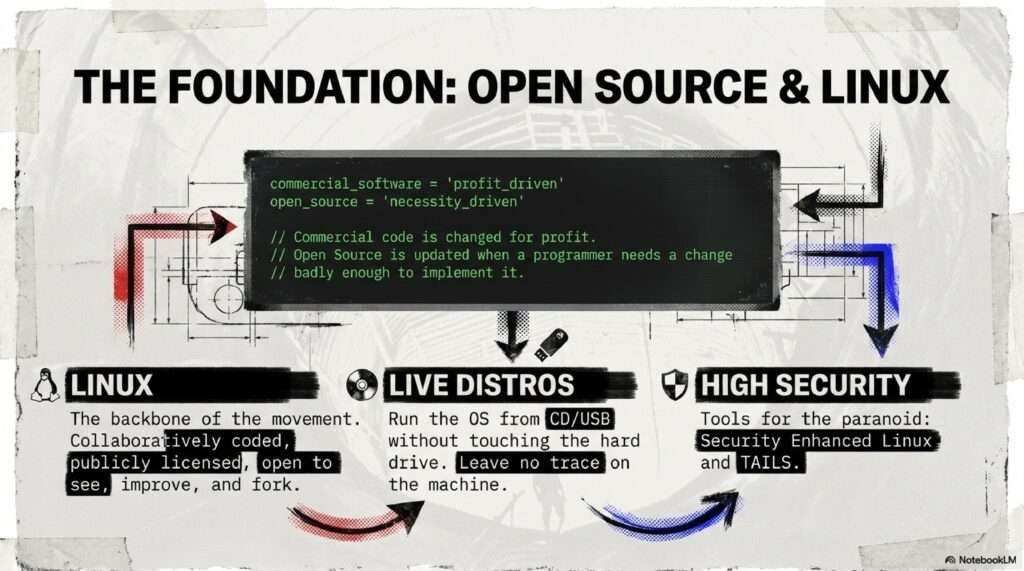
As surveillance becomes a subcontracted industry, traditional firewalls are no longer enough. You must adopt “Amnesic Computing”—using systems like TAILS 7.4 that leave no physical trace of your activity. By rotating your digital signatures and utilizing Zero-Knowledge proofs, you can navigate the web without ever revealing your underlying data.
“In an age of total surveillance, the only way to remain seen is to become unresolvable.”
3. Technical Sidebar: The Toolkit
-
OS: TAILS 7.4 (Amnesic Live System)
-
Network: Tor (Onion Routing) & I2P (Garlic Routing)
-
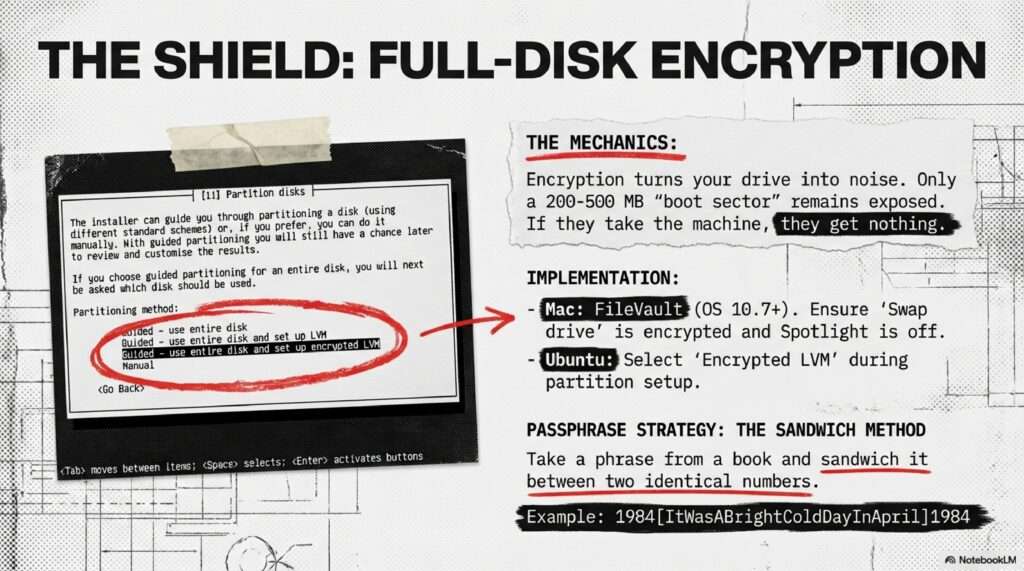
Encryption: LUKS with Detached Headers for FDE
-
Comms: XMPP with OTR (Off-the-Record) Plugin