The New Digital Frontier: Architecting Your Defense
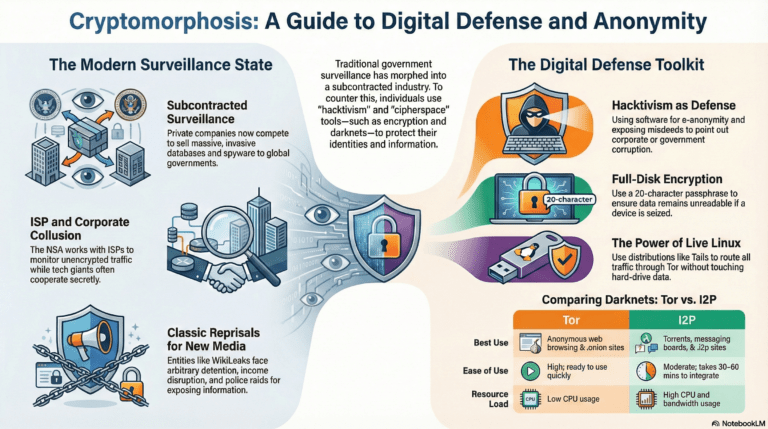
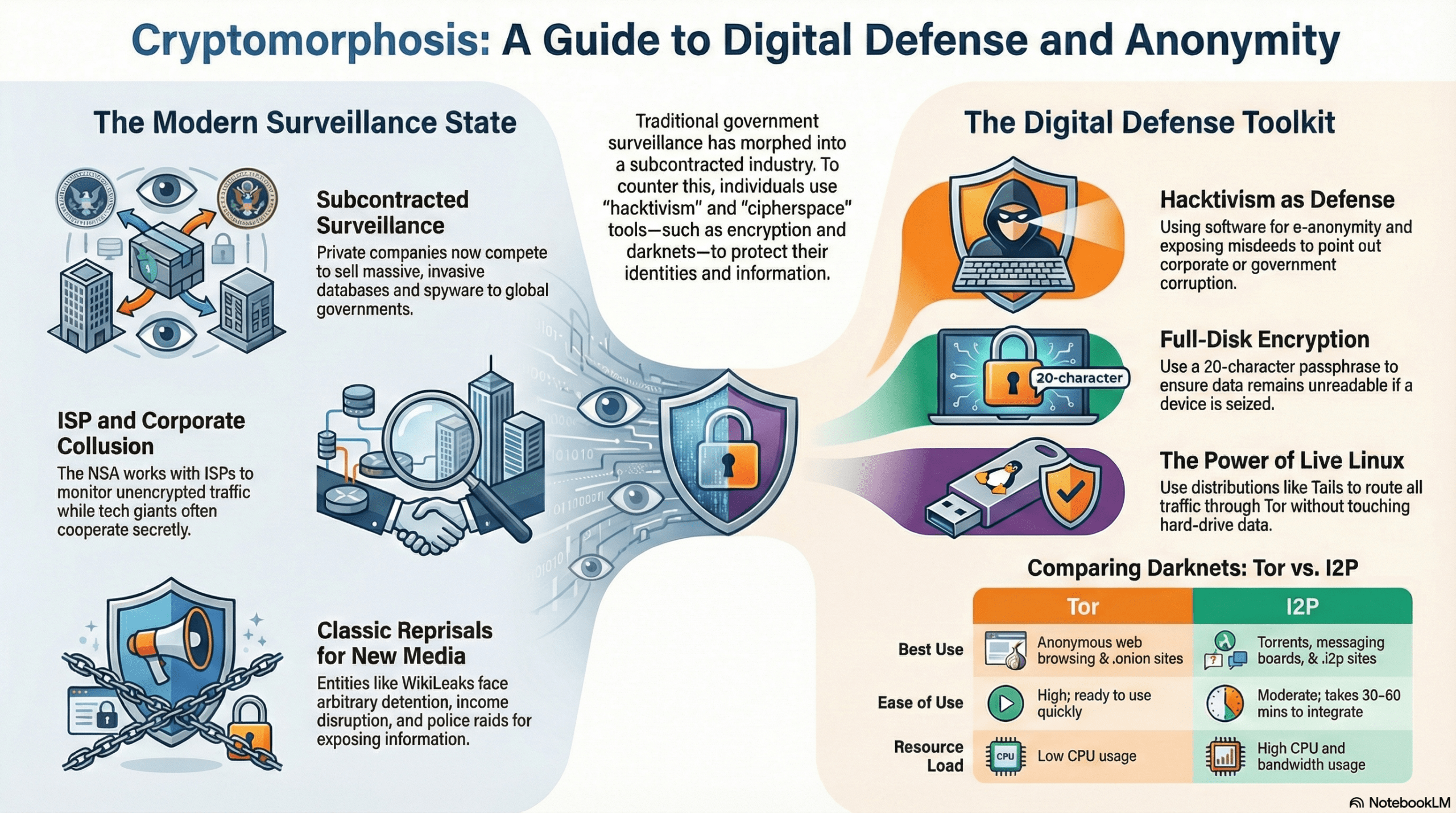
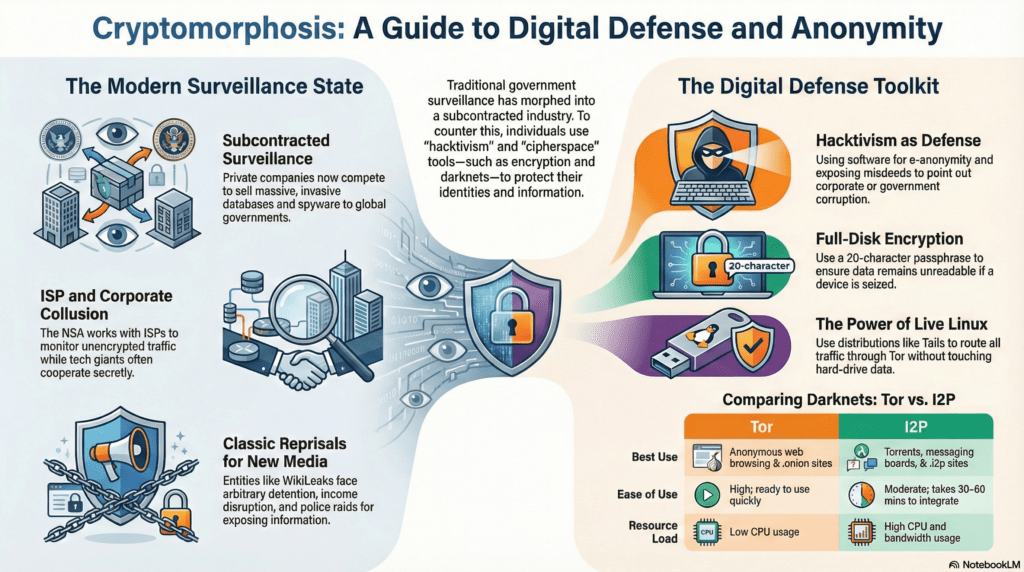
The digital landscape of 2026 is no longer a neutral territory; it is a surveilled marketplace where privacy must be actively engineered. As the world shifts from paper bureaucracies to AI-driven observation, remaining anonymous is a tactical necessity.
The Foundations of Cipherspace
To operate securely in the modern underworld, your network must be built on the principle of Zero-Trust. This involves layering multiple defensive protocols to ensure that even if one node is compromised, your core identity remains shielded.
-
Verified No-Log VPNs: Use only providers with a history of surviving judicial subpoenas without disclosing data.
-
Amnesic Operating Systems: Deploy TAILS 7.4 for high-stakes operations, ensuring all data is wiped from RAM upon shutdown.
-
Encrypted LVM: Full-disk encryption is mandatory to prevent physical data seizure.
Choosing Your Path: Tor vs. I2P
The choice between The Onion Router (Tor) and the Invisible Internet Project (I2P) depends on your mission profile. While Tor is the gold standard for anonymous browsing of the surface web, I2P offers a superior decentralized experience for internal darknet communications and file sharing.
The Cypherpunk Toolkit
Strategic defense requires a hardened browser profile. Essential 2026 extensions include:
-
NoScript & HTTPS-Everywhere: To prevent malicious script execution and force secure connections.
-
uBlock Origin: For advanced content filtering and tracker blocking.
-
Certificate Patrol: To detect man-in-the-middle attacks on your SSL/TLS connections.